- Cookies that enable provisioning of services you require.
- Cookies that inform NIC.LV about your visit on the website www.nic.lv - your consent is necessary for use of these cookies.
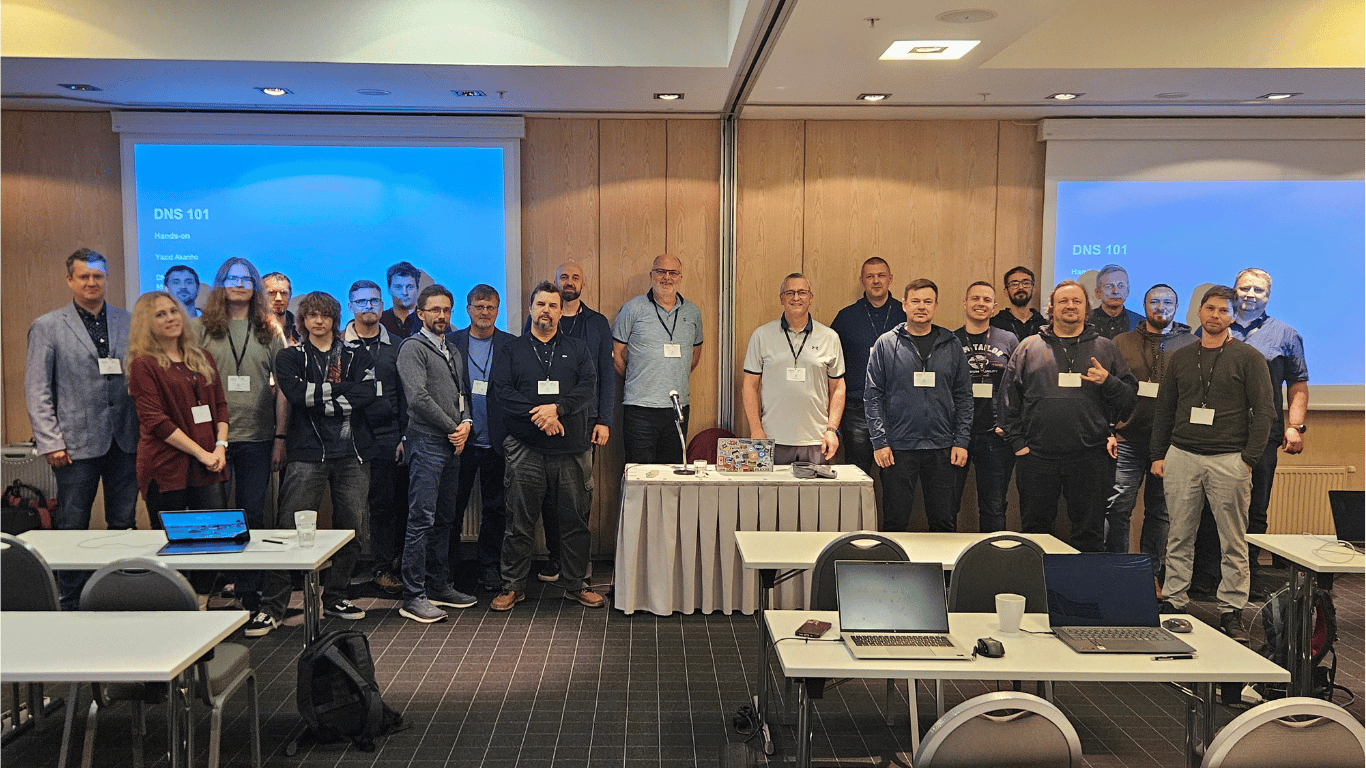
On Friday, October 31, a free one-day hands-on workshop on DNS security and DNSSEC (Domain Name System Security Extension) took place at Tallink Hotel Latvija, organized by CERT.LV, NIC, and ICANN (Internet Corporation for Assigned Names and Numbers).
The event brought together IT specialists, system administrators, and other technology professionals to gain in-depth, practical knowledge about DNS-related risks, DNSSEC implementation, and strengthening domain name security.
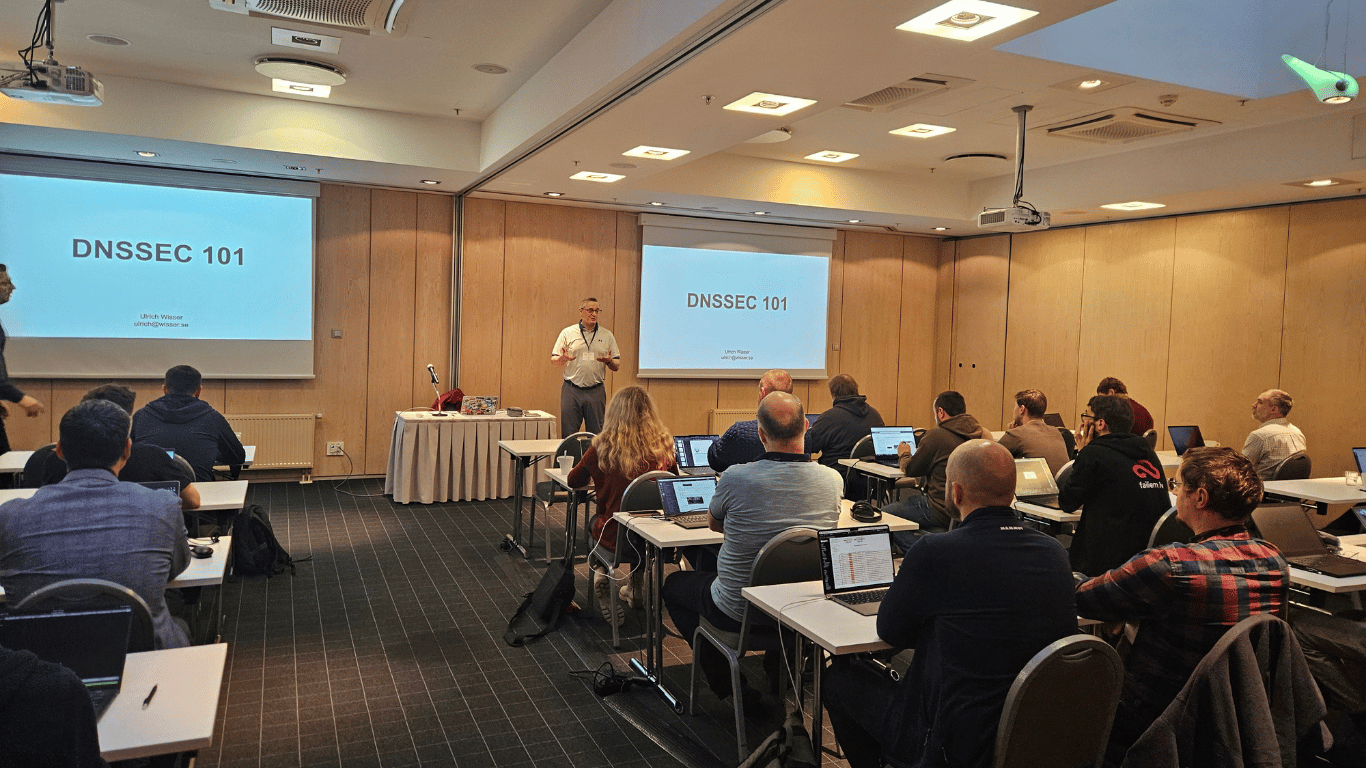
During the workshop, participants learned how to implement DNSSEC, sign zones, manage encryption keys, build a chain of trust, and validate DNSSEC on recursive servers. The day combined theory and practice, helping participants better understand DNS security principles and their role in maintaining a safe and reliable Internet infrastructure.
A special thank you to Ulrich Wisser, ICANN’s Technical Engagement Manager for Europe, for his high-quality content, practical insights, and knowledge sharing!
We also thank all participants for their engagement, questions, and contributions to an important discussion on DNS security in Latvia.
In today’s digital world, a company’s reputation and customer trust start with a secure domain name and a reliable email system. To protect your brand online and prevent fraud, it’s essential to implement two key mechanisms — email authentication and DNSSEC.
Email remains one of the most common tools exploited by cybercriminals. Through fake or spoofed emails, attackers can steal sensitive information, deceive clients, or damage a company’s reputation.
Three main technical protection mechanisms:
By implementing these three steps, organizations can significantly reduce email spoofing risks, protect their customers, and improve their domain’s name email reputation.
Your customers trust that, when they type in your company’s web address, they’ll reach your authentic website — not a fraudulent copy.
DNSSEC (Domain Name System Security Extensions)** protects your domain name by ensuring visitors actually reach your legitimate site. DNSSEC adds digital signatures to DNS records, preventing them from being silently modified. This protects against:
DNSSEC complements other security mechanisms (such as SSL/TLS) by strengthening the integrity of the domain name system itself.
Learn more: https://www.nic.lv/en/dnssec-en